Disable TLS 1.0 & 1.1
TLS (Transport Layer Security) is a cryptographic protocol used to secure communications over a channel or connection. It replaces the now deprecated SSL (Secure Socket Layer) standard. The IETF (Internet Engineering Task Force) is the group who publishes this standard and has, since its initial release, put out four version:
- TLS 1.0 (1999)
- TLS 1.1 (2006)
- TLS 1.2 (2008)
- TLS 1.3 (2018)
Both TLS 1.0 and 1.1 are now considered deprecated (2021) and should no longer be used in a modern network. In this article, we’ll walk through disabling TLS 1.0 and 1.1 using a free product called IIS Crypto, produced by Nartec Software.
Preparations
Prior to disabling TLS, audit your environment of services which interact with Active Directory via TLS but are limited to TLS version 1.0 and 1.1. Some things I’ve learned through my own experiences:
- Active Directory itself has no problem with TLS 1.0 and 1.1 disabled. This is assuming an up-to-date Windows Server 2016 or above operating system.
- The Microsoft Entra Connect service works with TLS 1.0 and 1.1 disabled.
- Check and confirm each service which relies on LDAPS for communications to the DC. Most modern software solutions should work without issue.
Instructions
When ready, walk through these steps to disable TLS 1.0 and 1.1.
Download Software
On each domain controller download the IIS Crypto software. This software is a portable executable and does not need to be installed on the domain controller.
Configure TLS Parameters
Next, we’ll configure which version we’d like enabled/disabled. Know that no changes will be made to the server until you select Apply.
- Open IIS Crypto.
- Under SChannel, select Best Practices.
- Deselect TLS 1.0 and TLS 1.1 under both Server Protocols and Client Protocols.
You should now see the following configuration:
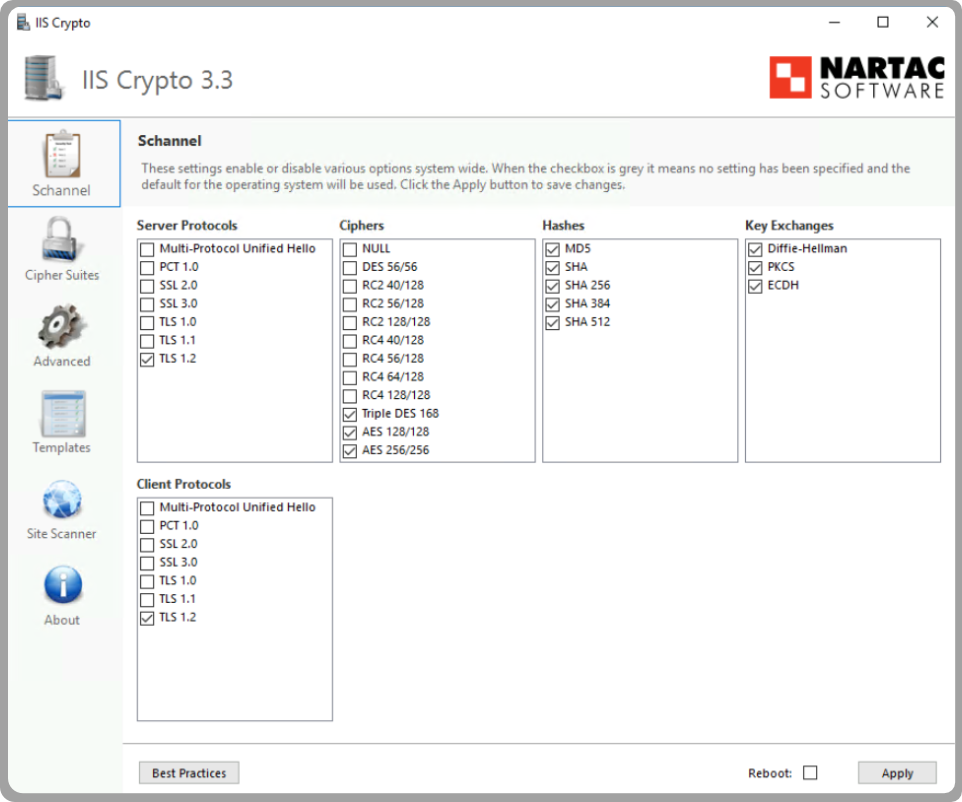
When ready, press Apply to have the select protocols/version enabled or disabled.
Reboot Server
Reboot the server to have the changes take effect.